Research
Share Knowledge
Brainstorm Ideas
Achieve More
According to a study by Cyber Risk Index (CRI) report, around 80% of global organizations are expecting data breaches that can impact their customer data within the next 12 months. The survey also mentions the three most negative consequences of having a security attack being:
The key findings of the report also indicate an increased rate of cyberattacks this year in comparison to their previous report.
Such findings only reinforce the urgent need for a better security strategy for most companies.
When companies set out to create a robust security strategy, they often tend to compromise on the customer experience. The more stringent protection a company offers, the harder it becomes for customers and users to access the services they need. However, it does not necessarily need to be this way.
Providing security to the end-users should almost be invisible, such that the customers are safe from all kinds of data breaches, credentials stuffing, and online fraud. With the evolution of technology, captcha solving, and deciphering codes and mathematics are getting more challenging for the customers, but malicious programs always have their way around.
The need of the hour is to incorporate technology that not only secures your customers but also stops bots, automated software, and malicious entities from engaging in abusive practices.
To implement security that also ensures a good customer experience, you must first define what a good user experience means to you. Remember that customer experience is not all about having a nice interface and quick resolution to queries. Cybersecurity lays the foundation of a company's IT infrastructure, revenue model, as well as customer experience.
Customers are constantly seeking simpler experiences, something companies should keep in mind while focusing on creating a secure environment. Apart from this, businesses should also look at cybersecurity as a means of building customer confidence. They can offer all the technical details and support to their end-users, without being too complex in their approach, thus ensuring a good customer experience too.
They should have clear objectives defined behind these three concerns:
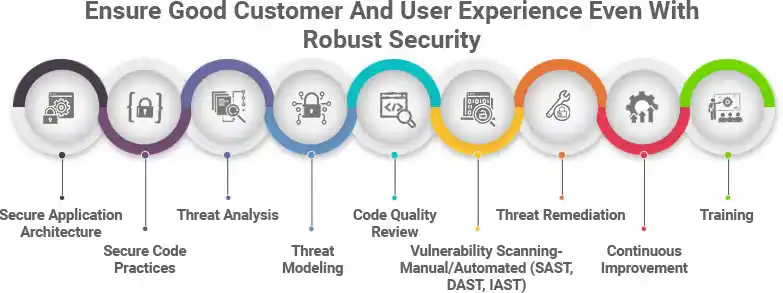
Agile application security solution experts like ITPN focus on reducing business risk and protecting customer data, without compromising the customer experience. They extensively use modern techniques and automation tools to create high-quality security processes. They create robust frameworks, designed such that they can monitor the evolution of vulnerabilities and take effective action to provide adequate protection to the end-users. Some of the most important services such expert providers offer are:
ITPN assists in creating applications that have security modules built into their architecture. Various elements like containers, secure engineering practices, network isolation, identity, and access management are incorporated to offer the best security solutions while keeping the applications fast and responsive.
To maintain utmost security, it is imperative to build a culture of security within the organization. This implies staying vigilant right from the start, by adopting secure coding practices and evolved process controls, even if the developers and employees do not have an in-depth understanding of security exploits and vulnerabilities. The collective team, right from the architecture design to testing, should maintain secure code practices so that there is no compromise with the user experience.
As the name suggests, threat analysis is the preliminary step to analyze all kinds of threats in the enterprise tech ecosystem. It helps in determining which components of the system require more security focus and the kind of security threats that they need protection from. Depending on the damage potential of the threat, the response priority and severity rating are determined.
Threat modeling is a crucial stage for maintaining security in applications as it focuses on the identification and mitigation of potential threats. Malicious threats like structural vulnerabilities or the absence of basic safeguards are identified at this stage, and all steps are prioritized to enumerate and mitigate the threat.
While creating custom enterprise applications, developers require an effective code review to ensure that their project is free from bugs and errors. By improving the code quality at an initial stage of software development, the codebase becomes more stable, and you can get the highest quality of coding in the review phase. Companies often use static analyzers like Klocwork and Helix QAC to monitor the key quality metrics.
A reliable application security service provider like ITPN focuses on all-around security scanning and assessment. This is why, they effectively implement cutting-edge technology to ensure complete security, such as — Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Interactive Application Security Testing (IAST).
An active approach towards cybersecurity measures, threat remediation involves assessment of risks, identification of indicators, and flagging, prioritizing, and resolving threats cyclically. The main focus of threat remediation is to consider the context and make use of actionable data to take action on malware and threats.
It is also important to seek security solutions that come with a guarantee of constant improvement. You can focus on the customer experience and roll out updates for ease of access. If your security services are also constantly upgraded and improved, you can be assured of absolute data security.
Without good training, neither the manpower nor technology can excel in its performance. That is why companies want application security solutions that ensure complete training services too. This way, IT security will not be an afterthought, but integrated into the application created for the users solely.
Data security and good customer experience need not be mutually exclusive. With curated solutions from ITPN, data security will now not come at the expense of user experience. Rather, modern technologies can pave the way for maximum threat remediation with a smoother user experience.